Navigating Market Turbulence: The U.S. Dollar’s Decline and Economic Insights from April 11, 2024
Tháng 4 11, 2025U.S. Dollar Declines: Navigating the Forex Market Amid Tariff Tensions and Inflation
Tháng 4 11, 2025Recent Developments: How Chinese Imports Are Leveraged in Cyberattacks
Overview of Risks
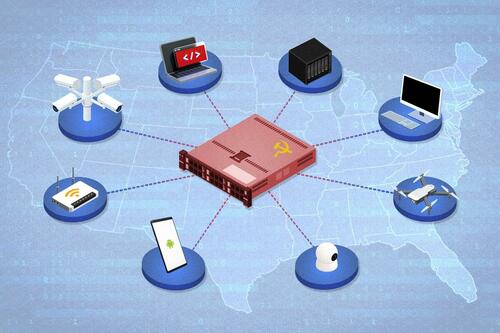
In the landscape of modern cybersecurity, the implications of Chinese imports, particularly technology products, have become a burgeoning concern for U.S. national security. Over recent years, it has been observed that these imports have increasingly been utilized as vectors for cyberattacks aimed at undermining American infrastructure and data safety. Attackers exploit vulnerabilities in widely distributed devices such as routers, security cameras, and storage systems, which can lead to unauthorized access to sensitive American networks. The frequency and sophistication of these cyber threats necessitate a keen awareness of the risks posed by imported Chinese technology.
Exploitation of Devices
Vulnerabilities in Chinese-made Devices are a significant focal point of risk. Many of these devices come with preinstalled malware or possess inherent security flaws that can be readily exploited by state-sponsored attackers. A recent example includes vulnerabilities discovered in equipment manufactured by Dahua Technology, a prominent player in the surveillance market, which has been implicated in Distributed Denial of Service (DDoS) attacks. These breaches not only compromise individual users but can also have ripple effects on broader networks, exposing critical infrastructure to exploitation.
The targeting of Critical Infrastructure is particularly alarming. Cyberattacks aimed at facilities such as power grids and port systems pose existential threats to national security. Compromised access to these essential services could disrupt daily life and economy, highlighting the dire consequences that may arise from the vulnerabilities embedded in devices sourced from China. The stakes are high as these threats continue to evolve, with attackers employing increasingly sophisticated techniques to bypass security protocols and infiltrate systems.
Escalation Due to Trade Tensions
The ongoing U.S.-China trade war has further exacerbated these risks, fostering an environment ripe for retaliation through cyberattacks. Speculation surrounds the potential use of cyber offensives as a strategic tool in the geopolitical arena, with recent incidents like the so-called “typhoon campaigns” — including operations named Salt Typhoon and Volt Typhoon — reported to have already gained access to critical U.S. infrastructure. This infiltration is concerning, as it suggests a preparatory phase for potentially destructive cyber engagements that could arise from escalated tensions.
Recent Admission and Escalation
In a surprising turn, Chinese officials have publicly acknowledged their involvement in cyber attacks against U.S. infrastructure, notably during a clandestine meeting where they discussed the Volt Typhoon operation. This admission serves as a striking reminder of the ongoing cyber warfare and geopolitical scheming prevalent today. Such a declaration is also interpreted as a veiled message intended to dissuade U.S. support for Taiwan, raising further questions about the intertwining nature of international relations and cybersecurity dynamics.
Cyber Fraud Amidst Trade Disputes
Amid the chaos brought about by trade disputes, there’s been a noticeable uptick in cyber fraud, with scammers increasingly leveraging the confusion surrounding tariffs. Phishing scams related to import costs have alarmingly surged, as fraudsters prey on individuals with fabricated shipping notices and phony tariff payment requests. This proliferation of cybercrime compounds the risks of trade tensions, illustrating how adversarial relations can spiral into broader vulnerabilities, affecting not just businesses but consumers as well.
In conclusion, as the digital landscape continues to evolve, the dangers posed by Chinese imports in cyberattacks are becoming increasingly pronounced. The intersection of technology, international trade, and cybersecurity merits greater scrutiny, necessitating a proactive approach to safeguard national interests against these emerging threats. The importance of fostering resilient cybersecurity frameworks cannot be overstated as they stand as the first line of defense against both current and future risks.